cryptography
[krip′täg·rə·fē]Cryptography
The various methods for writing in secret code or cipher. As society becomes increasingly dependent upon computers, the vast amounts of data communicated, processed, and stored within computer systems and networks often have to be protected, and cryptography is a means of achieving this protection. It is the only practical method for protecting information transmitted through accessible communication networks such as telephone lines, satellites, or microwave systems. Cryptographic procedures can also be used for message authentication, personal identification, and digital signature verification for electronic funds transfer and credit card transactions. See Data communications, Digital computer, Electrical communications
Cryptography helps resist decoding or deciphering by unauthorized personnel; that is, messages (plaintext) transformed into cryptograms (codetext or ciphertext) have to be able to withstand intense cryptanalysis. Transformations can be done by using either code or cipher systems. Code systems rely on code books to transform the plaintext words, phrases, and sentences into ciphertext code groups. To prevent cryptanalysis, there must be a great number of plaintext passages in the code book and the code group equivalents must be kept secret, making it difficult to utilize code books in electronic data-processing systems.
Cipher systems are more versatile. Messages are transformed through the use of two basic elements: a set of unchanging rules or steps called a cryptographic algorithm, and a set of variable cryptographic keys. The algorithm is composed of enciphering ( E ) and deciphering ( D ) procedures which usually are identical or simply consist of the same steps performed in reverse order, but which can be dissimilar. The keys, selected by the user, consist of a sequence of numbers or characters. An enciphering key (Ke) is used to encipher plaintext (X) into ciphertext (Y) as in Eq. (1), and a deciphering key (Kd) is used to decipher ciphertext (Y) into plaintext (X) as in Eq. (2). (1)  (2)
(2) 
Algorithms are of two types—conventional and public-key. The enciphering and deciphering keys in a conventional algorithm either may be easily computed from each other or may be identical [Ke = Kd = K, denoting E k(X) = Y for encipherment and D K(Y) = X for decipherment]. In a public-key algorithm, one key (usually the enciphering key) is made public, and a different key (usually the deciphering key) is kept private. In such an approach it must not be possible to deduce the private key from the public key.
When an algorithm is made public, for example, as a published encryption standard, cryptographic security completely depends on protecting those cryptographic keys specified as secret.
Unbreakable ciphers
Unbreakable ciphers are possible. But the key must be randomly selected and used only once, and its length must be equal to or greater than that of the plaintext to be enciphered. Therefore such long keys, called one-time tapes, are not practical in data-processing applications. To work well, a key must be of fixed length, relatively short, and capable of being repeatedly used without compromising security. In theory, any algorithm that uses such a finite key can be analyzed; in practice, the effort and resources necessary to break the algorithm would be unjustified.
Strong algorithms
Fortunately, to achieve effective data security, construction of an unbreakable algorithm is not necessary. However, the work factor (a measure, under a given set of assumptions, of the requirements necessary for a specific analysis or attack against a cryptographic algorithm) required to break the algorithm must be sufficiently great. Included in the set of assumptions is the type of information expected to be available for cryptanalysis. For example, this could be ciphertext only; plaintext (not chosen) and corresponding ciphertext; chosen plaintext and corresponding ciphertext; or chosen ciphertext and corresponding recovered plaintext.
A strong cryptographic algorithm must satisfy the following conditions: (1) The algorithm's mathematical complexity prevents, for all practical purposes, solution through analytical methods. (2) The cost or time necessary to unravel the message or key is too great when mathematically less complicated methods are used, because either too many computational steps are involved (for example, in trying one key after another) or because too much storage space is required (for example, in an analysis requiring data accumulations such as dictionaries and statistical tables).
To be strong, the algorithm must satisfy the above conditions even when the analyst has the following advantages: (1) Relatively large amounts of plaintext (specified by the analyst, if so desired) and corresponding ciphertext are available. (2) Relatively large amounts of ciphertext (specified by the analyst, if so desired) and corresponding recovered plaintext are available. (3) All details of the algorithm are available to the analyst; that is, cryptographic strength cannot depend on the algorithm remaining secret. (4) Large high-speed computers are available for cryptanalysis.
Digital signatures
Digital signatures authenticate messages by ensuring that: the sender cannot later disavow messages; the receiver cannot forge messages or signatures; and the receiver can prove to others that the contents of a message are genuine and that the message originated with that particular sender. The digital signature is a function of the message, a secret key or keys possessed by the sender of the message, and sometimes data that are nonsecret or that may become nonsecret as part of the procedure (such as a secret key that is later made public).
Digital signatures are more easily obtained with public-key than with conventional algorithms. When a message is enciphered with a private key (known only to the originator), anyone deciphering the message with the public key can identify the originator. The latter cannot later deny having sent the message. Receivers cannot forge messages and signatures, since they do not possess the originator's private key.
Since enciphering and deciphering keys are identical in a conventional algorithm, digital signatures must be obtained in some other manner. One method is to use a set of keys to produce the signature. Some of the keys are made known to the receiver to permit signature verification, and the rest of the keys are retained by the originator in order to prevent forgery.
Data Encryption Standard
Regardless of the application, a cryptographic system must be based on a cryptographic algorithm of validated strength if it is to be acceptable. The Data Encryption Standard (DES) is such a validated conventional algorithm already in the public domain. This procedure enciphers a 64-bit block of plaintext into a 64-bit block of ciphertext under the control of a 56-bit key. The National Bureau of Standards accepted this algorithm as a standard, and it became effective on July 15, 1977.
Block ciphers
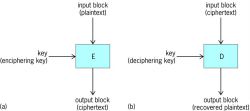
A block cipher (Fig. 1) transforms a string of input bits of fixed length (termed an input block) into a string of output bits of fixed length (termed an output block). In a strong block cipher, the enciphering and deciphering functions are such that every bit in the output block jointly depends on every bit in the input block and on every bit in the key. This property is termed intersymbol dependence.
Stream ciphers
A stream cipher (Fig. 2) employs a bit-stream generator to produce a stream of binary digits (0's and 1's) called a cryptographic bit stream, which is then combined either with plaintext (via the operator) to produce ciphertext or with ciphertext (via the -1 operator) to recover plaintext.
cryptography
(cryptography)The security of a cryptosystem usually depends on the secrecy of (some of) the keys rather than with the supposed secrecy of the algorithm. A strong cryptosystem has a large range of possible keys so that it is not possible to just try all possible keys (a "brute force" approach). A strong cryptosystem will produce ciphertext which appears random to all standard statistical tests. A strong cryptosystem will resist all known previous methods for breaking codes ("cryptanalysis").
See also cryptology, public-key encryption, RSA.
Usenet newsgroups: news:sci.crypt, news:sci.crypt.research.
FAQ MIT.
Cryptography glossary.
RSA cryptography glossary.
Cryptography, PGP, and Your Privacy.
cryptography
The encrypting (scrambling) of data into a secret code. Cryptography is used to conceal messages transmitted over public networks such as the Internet (see HTTPS). It is used to encrypt storage drives and messages so that only authorized users have access (see BitLocker, ScramDisk and digital signature).Cryptography is a major driver behind Bitcoin and blockchains, which hide the coin owner's identity in an encrypted address (see cryptographic hash function).
It's All Digital Today
Over the centuries, there have been many forms of cryptography, but today, all cryptographic processes are performed in a digital computer. See steganography.
From Plaintext to Ciphertext
A text message in its original form is called "plaintext." Using an encryption algorithm, the plaintext is turned into "ciphertext," which is indecipherable. To read the data, the ciphertext must be decrypted (unscrambled) and turned back into the original text (see plaintext).
Keys Are the Key
The encryption algorithm uses a "key," which is a binary number that is typically from 40 to 256 bits in length. The greater the number of bits in the key (cipher strength), the more possible key combinations and the longer it would take to break the code. The data are encrypted, or "locked," by combining the bits in the key mathematically with the data bits. At the receiving end, the key is used to "unlock" the code and restore the original data.
Secret vs. Public Key
Secret-key cryptography and public key cryptography are the two primary encryption architectures.
Secret Keys - Symmetric System
The first method uses a secret key, such as the DES and AES algorithms. Both sender and receiver employ the same key to encrypt and decrypt. This is the fastest computation method, but getting the secret key to the recipient in the first place is a problem that is often handled by the next method. See DES and AES.
Public Keys - Asymmetric System
The second method uses a two-part key, such as RSA and El Gamal. Each recipient has a private key that is kept secret and a public key that is published for everyone. The sender looks up or is sent the recipient's public key and uses it to encrypt the message. The recipient uses the private key to decrypt the message and never publishes or transmits the private key to anyone. Thus, the private key is never in transit making it less susceptible to theft. See RSA.
Both Are Used Together
Secret key and public key systems are often used together, such as the AES secret key and the RSA public key. The secret key method provides the fastest decryption, and the public key method provides a convenient way to transmit the secret key. This is called a "digital envelope." For example, the PGP email encryption program uses one of several public key methods to send the secret key along with the message that has been encrypted with that secret key (see PGP).
Get Faster - Get Stronger
It has been said that any encryption code can be broken given enough time to compute all permutations. However, if it takes months to break a code, a war could be lost or a thief could have long absconded with stolen money. As computers get faster, encryption algorithms have to become stronger by using longer keys and more clever techniques (see quantum secure). See XOR, digital signature, digital certificate and chaff and winnow.
| Secret Key vs. Public Key |
|---|
| The secret method uses the same key to encrypt and decrypt. The problem is transmitting the key to the recipient in order to use it. The public key method uses two keys: one kept private and never transmitted, while the other is made public. Very often, the public key method is used to safely send the secret key to the recipient so that the message can be encrypted using the faster secret key algorithm. |
Some Public History About Secret Methods
The following is reprinted with permission from RSA Security, Inc.
In 1518, a Benedictine monk named Johannes Trithemius wrote "Polygraphiae," the first published treatise on cryptography. Later, his text "Steganographia" described a cipher in which each letter is represented by words in successive columns of text, designed to hide inconspicuously inside a seemingly pious book of prayer.
Polygraphiae and Steganographia attracted a considerable amount of attention not only for their meticulous analysis of ciphers but more notable for the unexpected thesis of Steganographia's third and final section, which claimed that messages communicated secretly were aided in their transmission by a host of summoned spirits.
As might be expected, Trithemius' works were widely renounced as having magical content - by no means an unfamiliar theme in cryptographic history - and a century later fell victim to the zealous flames of the Inquisition during which they were banned as heretical sorcery.
Cryptography
secret writing, a special system of changing ordinary writing for the purpose of making it intelligible only to a limited number of persons who know the system. Different methods of cryptography have been used for encoding military, diplomatic, business, illegal-political, and religious-heretical texts; they are also used in children’s guessing games, rebuses, and the like.
Cryptography has been known since very ancient times in the Orient, Greece, and Rome and in Russian texts from the 12th and 13th centuries. Besides its basic functions, cryptography was used in Old Slavonic manuscripts for distinguishing a religious text from commentaries, instructions to the reader, and so on, and as a magical device in exorcisms.
The basic known methods of cryptography are (1) use of another alphabet (such as the Glagolitic, Greek, or Latin alphabet in Russian texts); (2) changing the letters by adding marks or dropping parts of letters (what was called half-writing); (3) use of substitute symbols or numbers; (4) use of a different alphabetical order (what was called litoreia, for example) or of numbers corresponding to letters; (5) writing a text in the form of a certain design, sometimes concealed in another text (as an acrostic); (6) writing words in reverse order.
An inscription or document written cryptographically is called a cryptogram.
REFERENCE
Speranskii, M. N. Tainopis’ v iugoslavianskikh i russkikh pamiatnikakh pis’ma. Leningrad, 1929V. M. ZHIVOV [13–1289–]